WordPress exploit

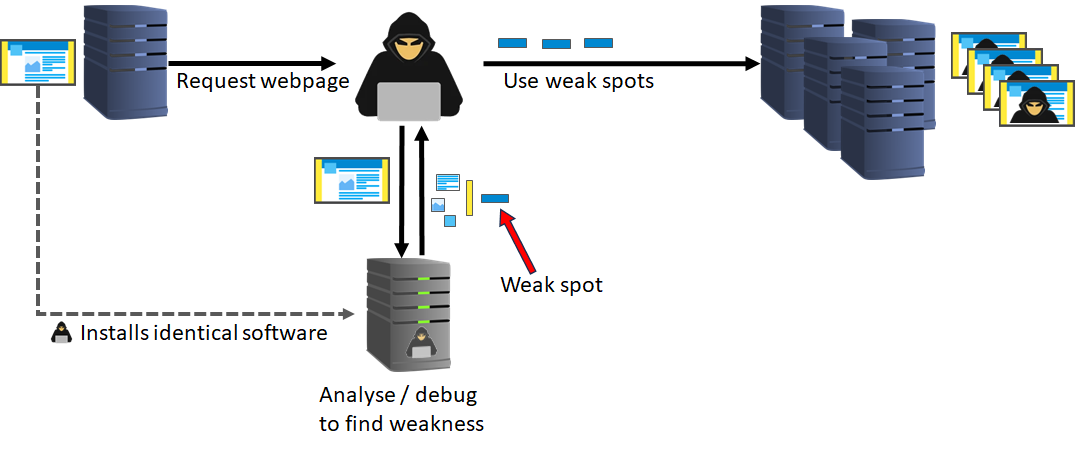
After finding quite a few older WordPress websites I wanted to see what a hacker could actually do. Although the number of exploits are well described on internet it still doesn't prove the hack is a real threat. Without hacking real websites I decided to install a version of various different WordPress sites on my own machine. Just to see what possibilities there actually are. Here are my first results:
WordPress version 4
There is a known vulnerability that allows a hacker to craft a website request that will result in a huge payload at the server itself. This exploit basically tells the server to send the whole dictionary back 1000 times and then repeat it over and over again. Normally a server will detect these kind of messages and block them. Unfortunately for the older versions of WordPress this is not the case and a hacker will keep a server so busy it cannot process any other requests. This results in a denial of service and the owner of the website ends up with a useless website. Here is my result:

Since I discovered quite a few websites that still use outdated WordPress versions I decided to get in contact with one of the owners. It would be great if they decide to upgrade their website due to me pointing out the risks. Sadly I received no response whatsoever. I wonder what will happen if I decide to publish my scan results? In the meantime my scanning software has identified at least 60 websites that are vulnerable to this exploit. So in theory I could down these websites, but I won't. Hopefully nobody will, but for a hacker this is all too easy. I'm glad that I was able to experiment with this, it gave me a good insight into hacking a website.
WordPress version 5
At the time of writing the latest version of WordPress is 6.8.1 and luckily most WordPress websites I scanned are up to date. Yet so many websites still use older versions. A well described vulnerability for WordPress 5.5.1 versions and lower allows attackers to fully take control of the website. But only those websites that use a particular extension. When this exploit was discovered there was no cure yet and once hackers got to know about this vulnerability it was massively used. To analyze this I setup a virtual environment using all the versions that were used.
After reading all information about the exploit I was able to alter the contents of my own website without having the proper rights to do so. So I hacked my own system.
I took the following steps (with the help of internet tutorials)